Asymmetric Encryption Processor Configuration
Asymmetric Encryption Processor encrypts input data using a supplied public key. Currently, it is distributed only in the United States.
Encrypt and Decrypt Data with the eiConsole’s Encryption and Decryption Processors.
The Encryption and Decryption Processors in the eiPlatform Integration Engine and eiConsole IDE provide a number of mechanisms that allow you to encrypt and decrypt data. As with all the components of the eiConsole, you are presented with a graphical interface with easy-to-configure panels. To configure the Encryption Processors on the Processor Configuration tab, click the Processor type drop-down list, and in the example below, select Asymmetric Encryption.
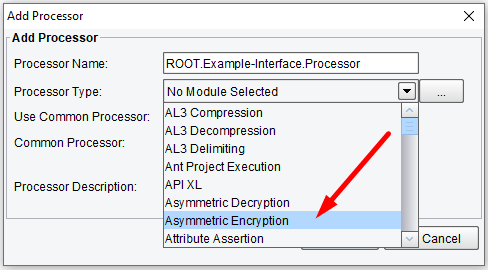
Processor (Adapter) Configuration Drop-Down List
Select the Asymmetric Encryption tab and click on Add Processor.
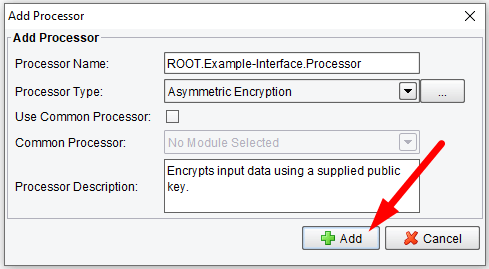
Click on Add Processor
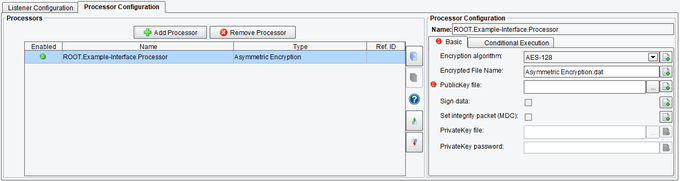
Basic Asymmetric Encryption Processor Configuration Options
The Basic tab allows you to set:
- Encryption Algorithm – allows specification of which encryption algorithm to utilize. There are 7 options: AES-128, AES-192, AES-256, BlowFish, CAST5, Triple-DES, TwoFish.
- Encrypted File Name – the file name to be used in the encryption
- PublicKey File – the “Public Key” for an encryption algorithm is a non-secure key that is linked to a secure key; this processor encrypts with the public key and only the private key can decrypt the data. Security is not guaranteed as it is dependent on the encryption algorithm.
- Sign Data – specifies whether or not to add a signature to the encrypted file
- Set Integrity Packet (MDC) – specifies whether or not to include the Modification Detection Code (MDC)
- PrivateKey File – The private key, which is used in this Processor specifically for signing encrypted files permits a higher degree of security
- PrivateKey Password – the password for the private key file
Asymmetric Encryption Processor Basic Configuration Options
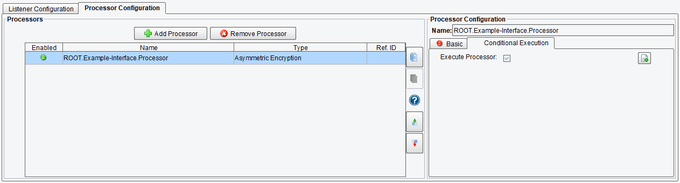
Conditional Execution Asymmetric Encryption Processor Configuration Options
On the Conditional Execution tab, you can set additional Processor execution conditions. The transaction data dependent condition may be specified here as an enhanced expression. If this expression returns anything other than TRUE (ignore case) – this processor will be skipped. No additional configuration for this Processor is required.
Asymmetric Encryption Processor Conditional Execution Configuration Options
For more information please call us at 860 632 9900 or click the link below.